Our VoIP and Network Security Methods
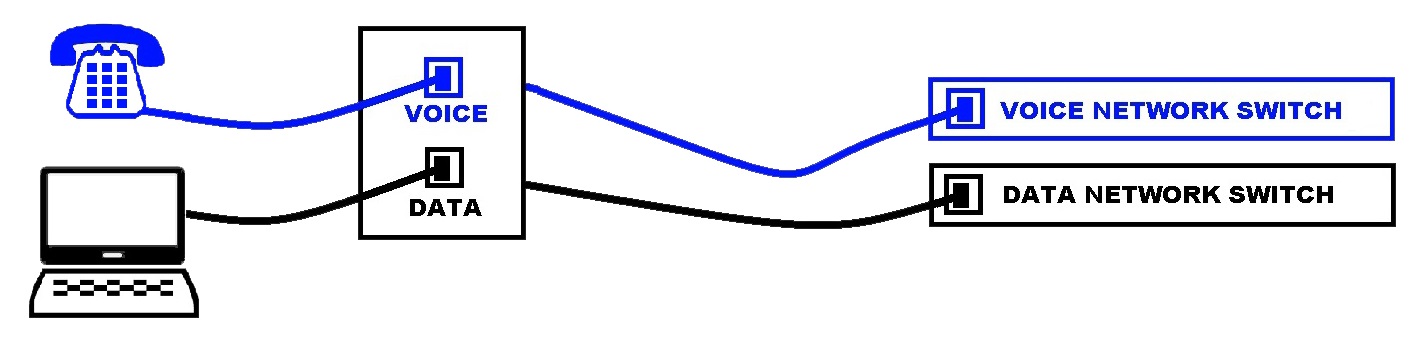
We separate voice and data networks and camera / POS systems for fault tolerance and security.
- Separate Ethernet cabling increase communication reliability. Separation allows you to call your IT people and say “our Internet phones work but our network does not”
- Separate Ethernet cabling increases security. Your PC data does not pass through a Chinese phone.
Most other companies choose to use one Ethernet cable “to save on cabling costs”. Companies come to us for telecommunications security. Below is how we secure VoIP communications.
| National VoIP Firms | Infotel Systems | |
|---|---|---|
| LAN | Phone and Computer share one Ethernet cable and one switch. | We install separate voice cabling to physically isolate the voice and data networks. |
| VOICE ENCRYPTION | No. Just unpack the phone and plug it in. | Yes. We always use encrypted SIP via a voice encryption router, VPN or other means. |
| CARRIER HOTELS | 90% of "Nationals" are on the West Coast. VoIP traffic goes through 3rd party "carrier hotels" that hand off from one carrier to another. | Your conversation NEVER leaves your Internet carrier (Verizon, Comcast, Cox). We are co-located with Verizon and one mile from the Comcast RVA hub. We call this "close cloud" , we are simply close to you Richmond. |
| PHONE PROVISIONING | Uses "Zero touch" install. Out of box phone first contacts a China provisioning server that registers your phone's ID and your business Internet IP address. | We use our own provisioning server in our data center. We never register phone with China. It never contacts China. It's more work. |
| SERVER ISOLATION | Huge virtualized servers. A server hack to one customer can provide a "vector" to other customers on that same server. | We don't do this and otherwise, no comment. |
| VOICE RECORDINGS | Stored on hosted servers. This was the data breach with Broadvoice | We offer on site "tap and store" of recordings. The data never leaves your premise. |
Here are just a few of the major data breaches in recent history
| Year | Company | Breach (Entry) Point | Damage |
|---|---|---|---|
| 2014 | Target Stores | 3rd party HVAC vendor's server | 40 million credit cards numbers compromised |
| 2019 | Broadvoice | Shared Voicemail server | 200,000 voicemail transcripts, customer data, etc |
| 2020 | Solar Winds | Software Update affected all who downloaded it | Data breach of government servers including Department of Treasury and Commerce |
Old Phone Service Was Secure, Some VOIP Systems Are Not
Your old phone system used analog lines. Analog is also known as (POTS) Plain Old Telephone Service. POTS has been a standard since Alexander Graham Bell. Many considered “POTS” impervious to hacking. Yet, most VoIP phone systems use unsecured Internet connections connected to your data network. VoIP provider Vonage states on this web page “.. do not use VoIP … use analog telephone lines instead as they are just harder to tap and extract the data from”
The Risk of Unsecured Voice – PCI (credit card) Example
Consider a sales person taking a credit card over your new Voice over Internet (VoIP) telephone system. The system does not feature VoIP audio encryption. Thus, the system fails the PCI 3.0 VoIP security requirement as ratified in November 2018. Therefore, you are subject to these fines. https://www.google.com/search?q=pci+fines
Articles on VoIP hacks
- https://www.networkworld.com/article/2349340/hackers-gain-access-to-private-hotel-network-using-cisco-voip.html
- https://www.bankinfosecurity.com/voip-phones-eavesdropping-alert-a-8869
- https://www.fdic.gov/news/financial-institution-letters/2005/fil6905.html
- https://www.defenseone.com/technology/2022/01/common-office-desk-phone-could-be-leaking-info-chinese-government-report-alleges/360500/
Industry Standards Security Review
- HIPAA requires voicemails, audio recordings and call reports to be protected. Unlike national providers, we can provide on premise audio recordings storage for the ultimate in compliance.
- PCI Telephone system VoIP security rules . We encrypt all VoIP traffic.
- FIRNA rule 4370 recommends business continuity systems such as 4G internet backup when Comcast fails. Rule 3170 covers voice recordings.
- NIST standards for VoIP security recommend separation of voice and data networks. A national VoIP company that ships phones in a box may not comply.
- SOX reflects NIST standards for data network protection.
Free Consult, Call 804-266-6600 or solutions@infotelsystems.com

